Data Security involves protecting digital data from unauthorized access, corruption, or theft throughout its lifecycle.
With increasing cyber threats and regulations, securing data is critical for trust and compliance.
Unauthorized access, data leakage, internal threats, and weak encryption.
With role-based access, data encryption, audit logs, masking, and secure data transfer protocols, ChainSys ensures robust protection.
Seamless Data Management & AI-Driven Insights – Empowering Your Enterprise with ChainSys Smart Solutions.







Unlock the full potential of your enterprise data with ChainSys’ Enterprise Data Management (EDM) solutions. Our Smart Data Platform ensures seamless data integration, governance, quality, and analytics, empowering businesses with trusted, high-quality data for smarter decision-making. With AI-driven automation, metadata intelligence, and a no-code/low-code approach, ChainSys simplifies data complexity, enhances compliance, and accelerates digital transformation. Turn your data into a strategic asset with ChainSys!

Migrate your enterprise data with confidence using ChainSys’ AI-driven Data Migration solutions. Our Smart Data Platform ensures a seamless, automated, and secure transition across legacy and modern systems while maintaining data integrity and minimizing downtime. With a metadata-driven, no-code/low-code approach, achieve faster, cost-effective migrations with repeatability and compliance. Move your data effortlessly and accelerate your digital transformation journey!

Ensure your enterprise operates with trusted, high-quality data using ChainSys’ Data Quality solutions. Leverage AI-powered cleansing, deduplication, validation, and enrichment to eliminate errors, inconsistencies, and redundancies. With real-time monitoring, rule-based automation, and intuitive dashboards, drive better decision-making and regulatory compliance. Clean data is powerful data—make every insight count!

Achieve complete data transparency, security, and compliance with ChainSys’ Data Governance solutions. Define and enforce policies, manage access controls, and ensure regulatory compliance with AI-driven automation. Our Smart Data Platform provides metadata-driven governance, enabling organizations to gain trust, mitigate risks, and unlock the true value of their data assets. Govern with confidence—govern with ChainSys!

Supercharge your data strategy with Active Metadata Management from ChainSys. Our AI-powered solution continuously captures, enriches, and operationalizes metadata for improved visibility, lineage tracking, and intelligent automation. Gain actionable insights, accelerate digital initiatives, and enhance collaboration with metadata-driven intelligence. Turn metadata into a competitive advantage with ChainSys!

Reduce storage costs, ensure compliance, and maintain easy access to historical data with ChainSys’ Data Archival solutions. Our automated, scalable, and policy-driven approach enables seamless data retirement while ensuring on-demand retrieval and compliance adherence. Optimize performance, free up resources, and keep your data ecosystem lean and efficient!
Transform raw data into actionable intelligence with ChainSys’ Data Analytics solutions. Leverage AI/ML-driven insights, real-time reporting, and intuitive dashboards to gain deeper business understanding and drive innovation. With seamless data integration and advanced visualization, empower your teams with data-driven decision-making for a competitive edge!

Break down data silos and enable seamless connectivity with ChainSys’ Data Integration solutions. Our metadata-driven, AI-powered platform ensures smooth, real-time data flow across cloud, on-premise, and hybrid environments. Gain unified, consistent, and reliable data across your enterprise for enhanced collaboration and efficiency. Connect, unify, and thrive with ChainSys!

Protect your most valuable asset—your data—with ChainSys’ Data Security solutions. Ensure enterprise-wide data protection, encryption, access controls, and regulatory compliance with AI-driven monitoring and proactive threat detection. Mitigate risks, prevent breaches, and safeguard sensitive information with confidence. Your data, your rules—stay secure with ChainSys!

Achieve a single source of truth with ChainSys’ Master Data Management (MDM) solutions. Establish consistency, eliminate duplicates, and ensure accuracy across your enterprise with a governed, AI-driven approach. Enable seamless collaboration, enhance business operations, and gain a trusted foundation for all your data-driven initiatives. Master your data, master your business with ChainSys!


ChainSys AMM automatically collects and catalogs metadata from various sources, including databases, data warehouses and cloud platforms. This continuous harvesting ensures that metadata is always up-to-date.

The platform provides comprehensive data lineage capabilities, allowing organizations to visualize the entire data journey from source to consumption. This helps in understanding dependencies and identifying potential issues.

By actively using metadata, ChainSys AMM supports automated data quality checks and validation processes. It ensures that data adheres to predefined quality standards before being used in critical operations.

ChainSys’s AMM uses metadata to enforce data governance policies automatically. It includes role-based access controls, policy enforcement, and compliance monitoring, ensuring that data is managed according to organizational rules and regulations.

The AMM seamlessly integrates with enterprise data catalogs, enabling a unified view of all data assets. This integration facilitates better data discovery, tagging, and collaboration across teams.

Tailored migration workflows allow organizations to define specific rules for data mapping, transformation, and validation based on business needs.

ChainSys AMM automatically collects and catalogs metadata from various sources, including databases, data warehouses and cloud platforms. This continuous harvesting ensures that metadata is always up-to-date.

The platform provides comprehensive data lineage capabilities, allowing organizations to visualize the entire data journey from source to consumption. This helps in understanding dependencies and identifying potential issues.

By actively using metadata, ChainSys AMM supports automated data quality checks and validation processes. It ensures that data adheres to predefined quality standards before being used in critical operations.

ChainSys’s AMM uses metadata to enforce data governance policies automatically. It includes role-based access controls, policy enforcement, and compliance monitoring, ensuring that data is managed according to organizational rules and regulations.

The AMM seamlessly integrates with enterprise data catalogs, enabling a unified view of all data assets. This integration facilitates better data discovery, tagging, and collaboration across teams.

Tailored migration workflows allow organizations to define specific rules for data mapping, transformation, and validation based on business needs.

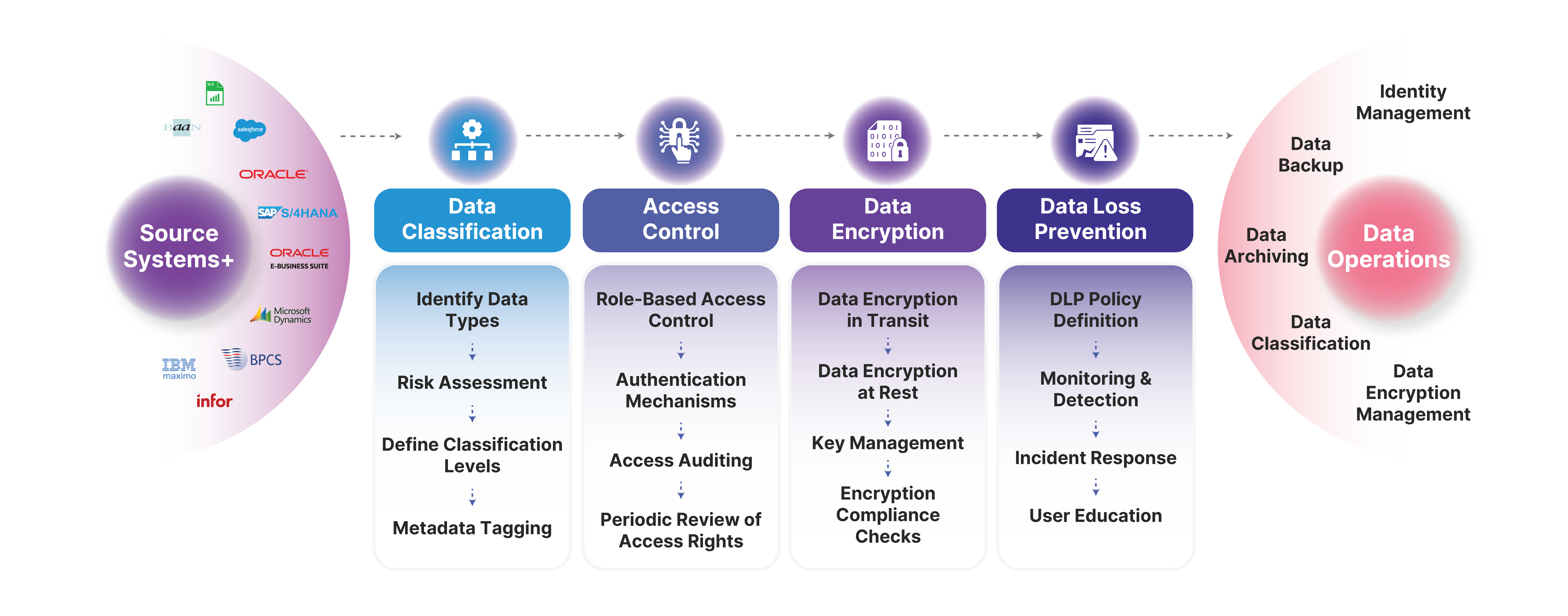
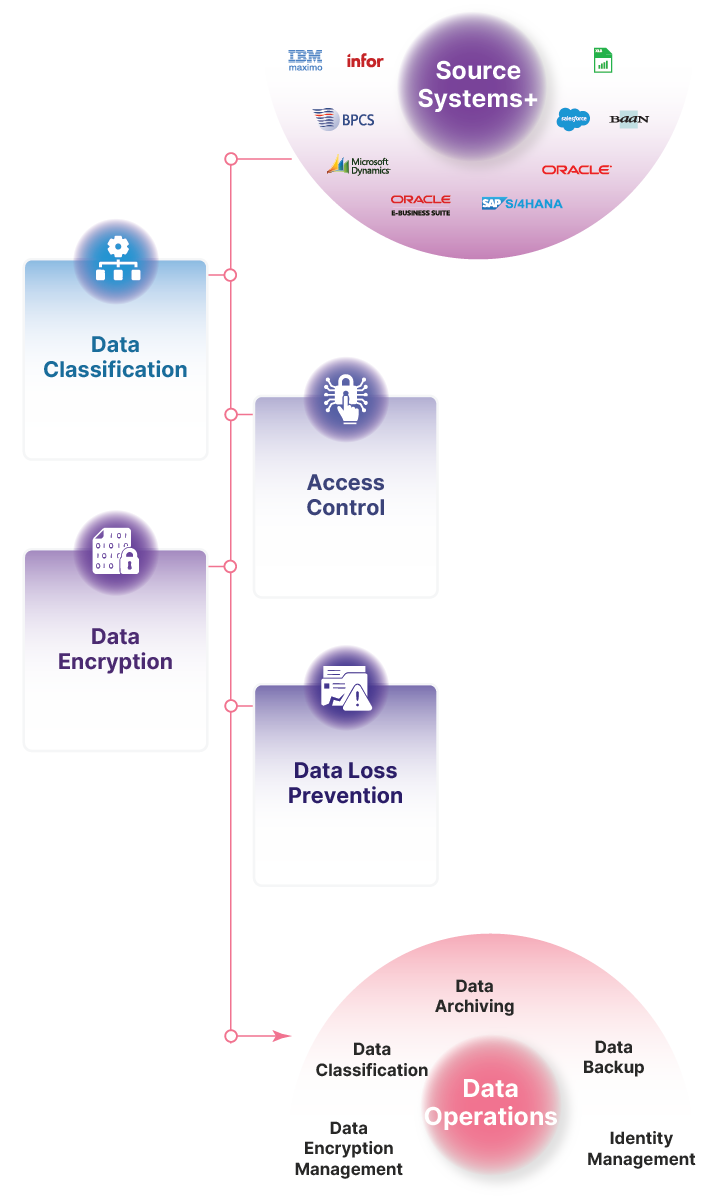
ChainSys Data Security offers end-to-end encryption for data at rest and in transit, along with secure key management practices to protect encryption keys from unauthorized access.

The platform includes advanced access control features, such as role-based access control (RBAC), multi-factor authentication, and single sign-on (SSO), to ensure that only authorized users can access sensitive data.

ChainSys offers tools for conducting regular security audits and generating compliance reports, helping organizations demonstrate adherence to security policies and regulatory requirements.

The platform includes data masking and anonymization features, allowing organizations to protect sensitive data during development, testing, and other non-production activities without exposing real data.
ChainSys AMM automatically collects and catalogs metadata from various sources, including databases, data warehouses and cloud platforms. This continuous harvesting ensures that metadata is always up-to-date.

The platform provides comprehensive data lineage capabilities, allowing organizations to visualize the entire data journey from source to consumption. This helps in understanding dependencies and identifying potential issues.

By actively using metadata, ChainSys AMM supports automated data quality checks and validation processes. It ensures that data adheres to predefined quality standards before being used in critical operations.

ChainSys’s AMM uses metadata to enforce data governance policies automatically. It includes role-based access controls, policy enforcement, and compliance monitoring, ensuring that data is managed according to organizational rules and regulations.

The AMM seamlessly integrates with enterprise data catalogs, enabling a unified view of all data assets. This integration facilitates better data discovery, tagging, and collaboration across teams.

The platform provides analytics and reporting on metadata, allowing organizations to monitor data quality trends, governance adherence, and usage patterns in real time.

Secure your enterprise data with ChainSys’ multilayered security framework.
Want bulletproof data defense?
ChainSys Data Security solutions provide comprehensive protection against data breaches, unauthorized access, and other security threats, ensuring the integrity and confidentiality of your data.
By implementing ChainSys Data Security, organizations can easily adhere to regulatory requirements and industry standards, minimizing the risk of compliance breaches and associated penalties.
ChainSys enables secure collaboration across teams and partners, ensuring that sensitive information can be shared safely without compromising data security.
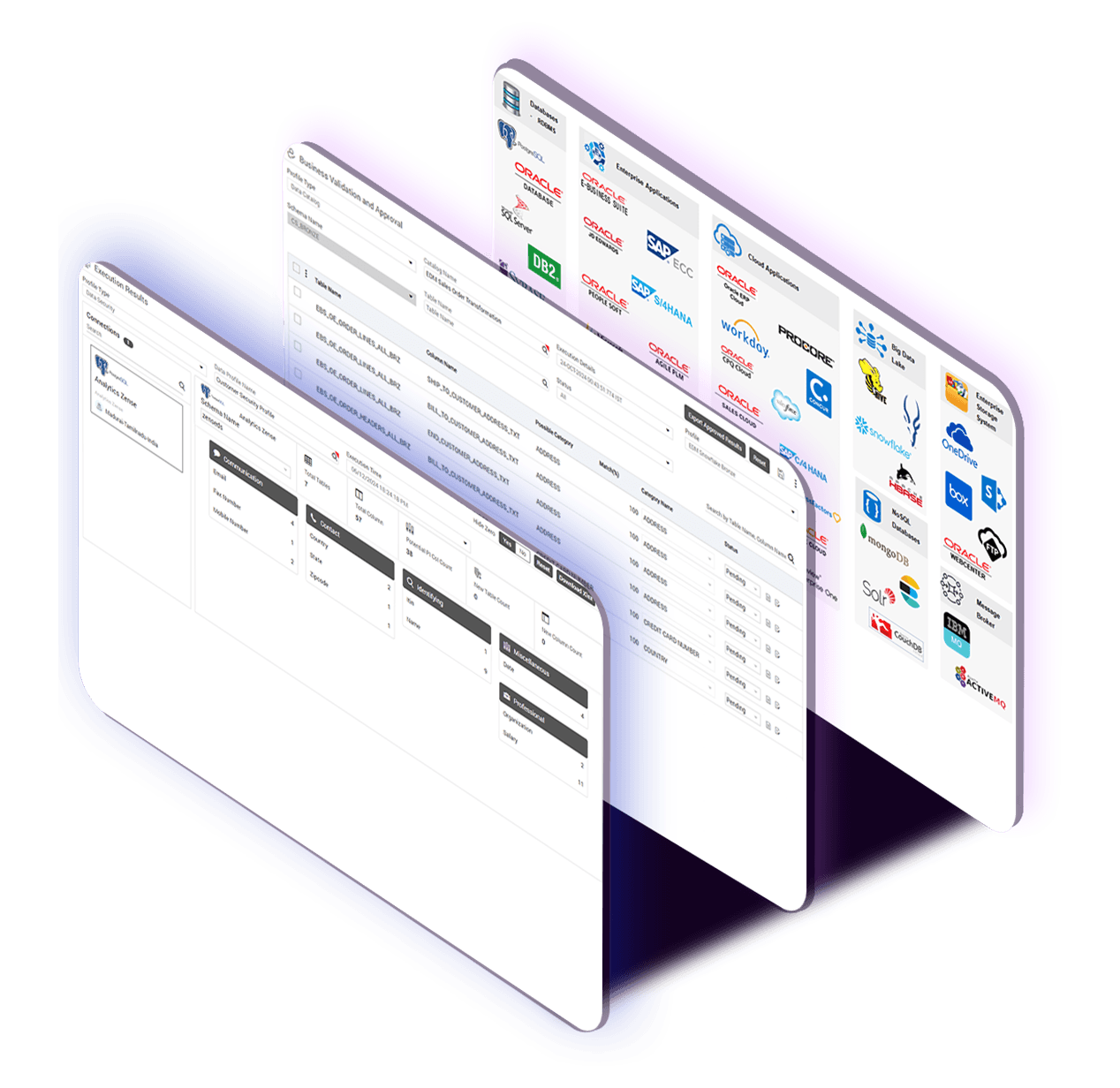
Connect effortlessly to 200+ endpoints across enterprise and cloud.









































































































Our platform is meticulously designed to provide a seamless integration experience, ensuring your data flows effortlessly across a diverse array of applications. Experience the unparalleled ease of connecting with over 200 applications effortlessly.










































































































ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With ChainSys's pre-built connectors and templates, businesses can implement active metadata management solutions 50% faster than traditional methods.
ChainSys has safeguarded over 1 billion records across 1,000+ enterprise projects globally, showcasing its robust and reliable data security measures.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With 256-bit encryption, multi-factor authentication, and real-time monitoring, ChainSys ensures that sensitive data remains secure, preventing unauthorized access and data breaches.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With ChainSys's pre-built connectors and templates, businesses can implement active metadata management solutions 50% faster than traditional methods.
ChainSys solutions are designed to comply with major global security standards, including GDPR, HIPAA, and ISO/IEC 27001, ensuring that your data security practices meet international regulations.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With ChainSys's pre-built connectors and templates, businesses can implement active metadata management solutions 50% faster than traditional methods.
ChainSys enjoys a 98% client retention rate in its data security services, highlighting the trust clients place in its ability to protect their critical data assets.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With ChainSys's pre-built connectors and templates, businesses can implement active metadata management solutions 50% faster than traditional methods.
ChainSys security solutions are built to scale with your organization, effectively managing and securing data environments of any size, from small businesses to large enterprises.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With ChainSys's pre-built connectors and templates, businesses can implement active metadata management solutions 50% faster than traditional methods.
ChainSys has safeguarded over 1 billion records across 1,000+ enterprise projects globally, showcasing its robust and reliable data security measures.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With 256-bit encryption, multi-factor authentication, and real-time monitoring, ChainSys ensures that sensitive data remains secure, preventing unauthorized access and data breaches.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With ChainSys's pre-built connectors and templates, businesses can implement active metadata management solutions 50% faster than traditional methods.
ChainSys solutions are designed to comply with major global security standards, including GDPR, HIPAA, and ISO/IEC 27001, ensuring that your data security practices meet international regulations.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With ChainSys's pre-built connectors and templates, businesses can implement active metadata management solutions 50% faster than traditional methods.
ChainSys enjoys a 98% client retention rate in its data security services, highlighting the trust clients place in its ability to protect their critical data assets.
ChainSys's solutions increase data discovery efficiency by 75%, enabling quicker access to relevant data assets and reducing the time spent on manual searches.
With ChainSys's pre-built connectors and templates, businesses can implement active metadata management solutions 50% faster than traditional methods.
ChainSys has facilitated GDPR, CCPA, and OIOO compliance for major enterprises, with clients achieving global implementation of PII identification in less than 6 months.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
